This was run on Metasploit using auxiliary scanner.Below is the step taken.
msf > search nbname
[*] Searching loaded modules for pattern 'nbname'...
Auxiliary
=========
Name Rank Description
---- ---- -----------
scanner/netbios/nbname normal NetBIOS Information Discovery
scanner/netbios/nbname_probe normal NetBIOS Information Discovery Prober
msf > use auxiliary/scanner/netbios/nbname
msf auxiliary(nbname) > show options
Module options:
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
CHOST no The local client address
RHOSTS yes The target address range or CIDR identifier
RPORT 137 yes The target port
THREADS 1 yes The number of concurrent threads
msf auxiliary(nbname) > set RHOSTS 192.168.0.1/24
RHOSTS => 192.168.0.1/24
msf auxiliary(nbname) > run
RESULT AS SHOWN BELOW
[*] Sending NetBIOS status requests to 192.168.0.0->192.168.0.255 (256 hosts)
[*] 192.168.0.154 [DELL-PC] OS:Unix Names:(DELL-PC, WORKGROUP) Addresses:(192.168.0.154) Mac:00:00:00:00:00:00
[*] 192.168.0.201 [DELL-PC] OS:Unix Names:(DELL-PC, WORKGROUP) Addresses:(192.168.0.201) Mac:00:00:00:00:00:00
[*] 192.168.0.226 [] OS:Windows Names:() Mac:c2:5e:38:76:b9:53
[*] 192.168.0.194 [ASPIRE-4736Z] OS:Windows Names:(ASPIRE-4736Z, WORKGROUP, __MSBROWSE__ ) Addresses:(192.168.0.194) Mac:00:a0:c6:00:00:00
[*] 192.168.0.130 [USER-C647DE9D52] OS:Windows Names:(USER-C647DE9D52, WORKGROUP, __MSBROWSE__ ) Mac:00:1e:10:1f:03:4e
[*] 192.168.0.163 [USER] OS:Windows Names:(USER, WORKGROUP) Addresses:(192.168.0.163) Mac:00:a0:c6:00:00:00
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
Tuesday, August 17, 2010
Wednesday, August 11, 2010
Monday, August 2, 2010
August Updates..??
Sorry guys I seldom updates my blog..Is anybody out there watching my blog?har har har ..who cares as long I can update its.. :D
Now I teach you all how to do a SPAN Port to monitor / or sniffing :-
Of Course In CISCO wayss.. :P
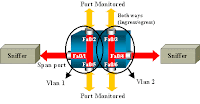
Configuration Steps Explanation
In order to configure port Fa0/1 as a destination port, the source ports Fa0/2 and Fa0/5, and the management interface (VLAN 1), select the interface Fa0/1 in the configuration mode:
Switch(config)#interface fastethernet 0/1
Enter the list of ports to be monitored:
Switch(config-if)#port monitor fastethernet 0/2
Switch(config-if)#port monitor fastethernet 0/5
With this command, every packet that these two ports receive or transmit is also copied to port Fa0/1. Issue a variation of the port monitor command in order to configure the monitoring for the administrative interface:
Switch(config-if)#port monitor vlan 1
Note: This command does not mean that port Fa0/1 monitors the entire VLAN 1. The vlan 1 keyword simply refers to the administrative interface of the switch.
This example command illustrates that the monitor of a port in a different VLAN is impossible:
Switch(config-if)#port monitor fastethernet 0/3
FastEthernet0/1 and FastEthernet0/3 are in different vlan
In order to finish the configuration, configure another session. This time, use Fa0/4 as a destination SPAN port:
Switch(config-if)#interface fastethernet 0/4
Switch(config-if)#port monitor fastethernet 0/3
Switch(config-if)#port monitor fastethernet 0/6
Switch(config-if)#^Z
Issue a show running command, or use the show port monitor command in order to check the configuration:
Switch#show port monitor
Monitor Port Port Being Monitored
--------------------- ---------------------
FastEthernet0/1 VLAN1
FastEthernet0/1 FastEthernet0/2
FastEthernet0/1 FastEthernet0/5
FastEthernet0/4 FastEthernet0/3
FastEthernet0/4 FastEthernet0/6
Note: The Catalyst 2900XL and 3500XL do not support SPAN in the Rx direction only (Rx SPAN or ingress SPAN) or in the Tx direction only (Tx SPAN or egress SPAN). All SPAN ports are designed to capture both Rx and Tx traffic.
Now I teach you all how to do a SPAN Port to monitor / or sniffing :-
Of Course In CISCO wayss.. :P

Configuration Steps Explanation
In order to configure port Fa0/1 as a destination port, the source ports Fa0/2 and Fa0/5, and the management interface (VLAN 1), select the interface Fa0/1 in the configuration mode:
Switch(config)#interface fastethernet 0/1
Enter the list of ports to be monitored:
Switch(config-if)#port monitor fastethernet 0/2
Switch(config-if)#port monitor fastethernet 0/5
With this command, every packet that these two ports receive or transmit is also copied to port Fa0/1. Issue a variation of the port monitor command in order to configure the monitoring for the administrative interface:
Switch(config-if)#port monitor vlan 1
Note: This command does not mean that port Fa0/1 monitors the entire VLAN 1. The vlan 1 keyword simply refers to the administrative interface of the switch.
This example command illustrates that the monitor of a port in a different VLAN is impossible:
Switch(config-if)#port monitor fastethernet 0/3
FastEthernet0/1 and FastEthernet0/3 are in different vlan
In order to finish the configuration, configure another session. This time, use Fa0/4 as a destination SPAN port:
Switch(config-if)#interface fastethernet 0/4
Switch(config-if)#port monitor fastethernet 0/3
Switch(config-if)#port monitor fastethernet 0/6
Switch(config-if)#^Z
Issue a show running command, or use the show port monitor command in order to check the configuration:
Switch#show port monitor
Monitor Port Port Being Monitored
--------------------- ---------------------
FastEthernet0/1 VLAN1
FastEthernet0/1 FastEthernet0/2
FastEthernet0/1 FastEthernet0/5
FastEthernet0/4 FastEthernet0/3
FastEthernet0/4 FastEthernet0/6
Note: The Catalyst 2900XL and 3500XL do not support SPAN in the Rx direction only (Rx SPAN or ingress SPAN) or in the Tx direction only (Tx SPAN or egress SPAN). All SPAN ports are designed to capture both Rx and Tx traffic.
Subscribe to:
Posts (Atom)